Report Materials
Why OIG Did This Audit
- From March 2023 through January 2024, bad actors fraudulently diverted $7.8 million in grant funds from HHS’s Program Support Center (PSC) grant payment system.
- Bad actors were able to gain access to the PSC grant payment system by masquerading as grant recipients and requesting account changes, including changes to grant recipients’ banking information.
- This audit reviewed PSC’s internal controls, risk management, and cybersecurity controls over the PSC grant payment system to determine whether the system was properly protected.
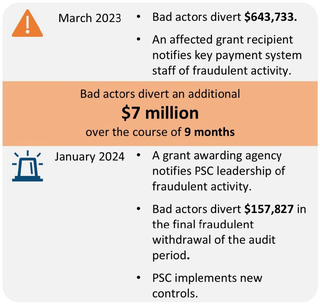
What OIG Found
- At the time of the fraud, PSC did not have effective internal controls to communicate fraudulent activity to PSC leadership, grant awarding agencies, and grant recipients.
- PSC’s approach to risk management was siloed and did not address the risk of bad actors gaining access to the payment system.
- PSC did not implement some required cybersecurity controls, including mitigating weaknesses timely and conducting required IT system vulnerability scans, reviews, and approvals.
PSC has begun to take steps to mitigate the future risk of fraud.
What OIG Recommends
We made six recommendations to improve PSC’s controls over its grant payment system, including that it implement additional cybersecurity controls, finalize and implement bank account verification processes, and develop standard operating procedures.
PSC concurred with all six of our recommendations.
View in Recommendation Tracker
Notice
This report may be subject to section 5274 of the National Defense Authorization Act Fiscal Year 2023, 117 Pub. L. 263.
